2.5 Connecting your domain to Cloudflare

CloudFlare is one of the world’s leading platforms for website optimization and protection. It’s a service that works as an intermediate layer between Your website and visitors, providing enhanced performance, security, and reliability. The platform offers a wide range of solutions, from accelerating page loading through a global content delivery network (CDN) to powerful protection against cyber attacks.
One of CloudFlare’s key features is DDoS attack protection, which automatically blocks malicious traffic, allowing Your site to remain accessible even under high-threat conditions. CloudFlare also provides HTTPS connection encryption capabilities, access control through web application firewalls (WAF), and intelligent traffic management. These features make CloudFlare an indispensable tool for site owners seeking stable and secure operation of their resources.
Important: before starting the setup, make sure of the following.
- You have access to the domain control panel at Your registrar.
- The domain is active and has no restrictions on changing NS servers.
- You have Your server’s IP address.
Step-by-Step Connection Guide
1. Registration and Obtaining CloudFlare NS Servers
Go to Cloudflare and create an account. After logging into Your account, click + Add ➔ Existing domain and enter Your domain. Select Quick scan for DNS records and wait for the existing DNS records to be scanned.

If no records are found, then create at least two basic A type records, for the main domain @ and for the alias www, direct these records to Your hosting IP address.

Additionally: check automatically imported DNS records Add missing records if necessary Configure proxy status for each record (orange cloud - enabled, gray - disabled)
Select a pricing plan (You can start with the Free plan).

2. Changing NS Servers at Your Registrar
CloudFlare will provide You with two NS servers that need to be configured at Your current registrar.
[details open If the domain is registered with TheHost:
If You purchased a domain from us and want to point it to CloudFlare, log into Your personal account, go to the Domain Names section, select the desired domain with Your mouse and click the Name Servers button. Make sure to activate the option Change domain NS servers.

If the domain is serviced by another registrar:
- Log into Your registrar’s domain control panel.
- Find the NS servers settings section.
- Replace the current NS servers with those received from CloudFlare.
- Save the changes.
Remember: if You have any other NS servers configured in the panel, You need to remove them and add only the records provided by CloudFlare. If You set up a mix of old and new servers – the domain will start working unstably.
3. Setting up DNS for Mail in CloudFlare Panel
Go to DNS ➔ Records, click + Add record.
Then add A, TXT, and MX records for proper mail functionality.

If DKIM or DMARC or any other records are used and auto-search didn’t find them, You’ll need to add these records manually as well. An example of mail record settings is demonstrated in our guide.
To save the added record, click Save.
Important: be especially careful when configuring DNS records, as errors can lead to site unavailability. It’s recommended to take a screenshot or save a copy of current settings before making changes.
SSL Certificate Setup
When connecting a domain to Cloudflare, two separate connections are created: from user to CloudFlare and from CloudFlare to Your hosting.
The first connection is automatically protected by a free SSL Universal certificate from CloudFlare. For complete protection, You need to configure encryption for the second connection as well.
Important to understand: full protection is only possible with an SSL certificate on Your hosting.
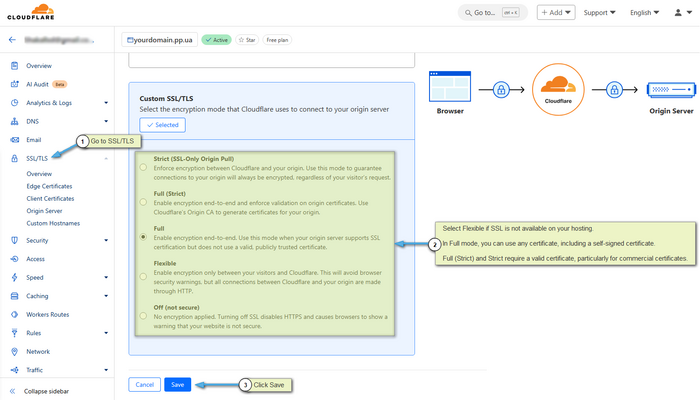
Encryption Modes
Which encryption mode to choose: in most cases, for proper site operation, You need to set one of the following encryption modes.
- Full Mode — if an SSL certificate is used on the hosting.
- Flexible Mode — if no SSL certificate is used on the hosting.
Detailed comparison of encryption modes.
1. Off:
- Complete lack of encryption.
- Not recommended for use.
- Site is only accessible via HTTP.
2. Flexible:
- Encryption only between user and CloudFlare.
- Data between CloudFlare and hosting is transmitted unprotected.
- Suitable as a temporary solution.
- Users see HTTPS in browser.
Warning regarding Flexible mode:
- Use only temporarily.
- There is a risk of data interception.
- It’s recommended to install SSL on hosting as soon as possible.
3. Full:
- Encryption on both connection segments.
- Requires SSL certificate on hosting.
- Medium security level.
- Accepts even self-signed certificates.

4. Full (Strict):
- Maximum security level.
- Requires valid SSL certificate on hosting.
- Verifies certificate authenticity.
- Recommended mode when having a commercial SSL.
Important: if there is no SSL certificate on the hosting, do not enable Full or Full (Strict) modes. This will lead to errors.
- Error 525: SSL connection problem.
- Error 526: Invalid SSL certificate.
Additional Security Settings
If You notice accessibility issues or clients complain that sites don’t open for everyone, You can use additional settings such as forced HTTPS traffic redirect, minimum TLS version support, or improved compatibility with older browsers.
- Always Use HTTPS:
- Go to SSL/TLS ➔ Edge Certificates.
- Enable the Always Use HTTPS option.
- Provides automatic redirection from HTTP to HTTPS.

-
Minimum TLS Version:
- Recommended to set TLS 1.2 or higher.
- Provides modern security standards.
- Reduces the risk of using vulnerable protocols.
-
Opportunistic Encryption:
- Improves compatibility with older browsers.
- Provides an additional layer of protection.
- Recommended to keep enabled.
How to Protect Your Site from DDoS Attacks
Connecting Your site to CloudFlare already provides basic protection against DDoS attacks. The platform hides Your server’s IP address and redirects all traffic through its secure servers. This allows blocking malicious traffic before it reaches Your hosting.
Content caching also significantly reduces the load on Your hosting during attacks. However, for maximum protection, it’s recommended to configure additional security parameters in Your Cloudflare account.
Important to know: CloudFlare’s free plan helps protect the site only from the simplest attacks. For protection against complex attacks, it’s recommended to consider paid plans.
“I’m Under Attack!” Mode
The I’m Under Attack! mode is one of the most powerful tools for DDoS attack protection in CloudFlare. When activated, the system applies multi-level verification to each visitor.
Important: turning on I’m Under Attack! can lead to a significant increase in the load on the hosting. Since all traffic from IP addresses will go through Cloudflare directly to our server, this concentration of load cannot be efficiently handled at the hosting level. This can negatively affect the performance of your site.
You can enable it in the Security ➔ Settings ➔ Security Level section.

-
Initial Check:
- Visitor first sees an intermediate page with the message DDoS protection by CloudFlare.
- System performs automatic analysis of visitor’s browser.
- Check lasts 5-10 seconds.
-
Verification Process:
- Browser behavior is analyzed.
- JavaScript functionality is checked.
- Request speed and patterns are evaluated.
- Bot presence is checked.
-
Check Results:
- Upon successful verification, visitor gets access to the site.
- When suspicious activity is detected, request is blocked.
- Legitimate users receive temporary access (30 minutes by default).

Check Time Settings:
- The Challenge Passage parameter determines how long a user will have access after successful verification.
- Recommended values: 15 to 45 minutes.
- During strong attacks, can be reduced to 15 minutes.
- During quiet times, can be increased to several hours.
When to Use “I’m Under Attack!”
Recommended Usage Scenarios:
- During active DDoS attacks.
- When sudden increase in suspicious traffic occurs.
- When standard protection measures aren’t helping.
- During massive password brute-force attempts.
Important Precautions:
- Mode can slow down access for legitimate users.
- Not recommended for constant use.
- Can affect API and external services operation.
- Should be disabled after attack ends.
Alternative Protection Levels:
If full I’m Under Attack! mode is too aggressive, consider other security levels.
-
High:
- Checks only suspicious traffic.
- Shows verification to visitors from suspicious IPs.
- Less impact on legitimate users.
-
Medium:
- Balanced protection.
- Checks only very suspicious requests.
- Suitable for daily use.
-
Low:
- Minimal checks.
- Blocks only confirmed threats.
- For sites with low attack risk.
Firewall Rules Setup
Properly configured firewall rules are an important component of site protection against attacks and unwanted traffic. With CloudFlare tools, You can create flexible rules for blocking malicious requests, limiting access to certain resources, or allowing access only to trusted users.
The firewall works as a filter between Your site and visitors, analyzing each request. This allows detecting and blocking suspicious actions such as automated data collection attempts, password guessing, or excessive server load. Access rule configuration not only helps fight DDoS attacks but also provides additional flexibility for traffic management.
To create access rules:
- Go to Security ➔ WAF ➔ Custom rules.
- Click Create rule.
- Configure parameters:
- Rule name: rule name.
- Field: filtering parameter (IP address, Country, User Agent).
- Operator: trigger condition.
- Value: filtering value.

Additional Rule Capabilities:
- Geographic-based blocking.
- User Agent filtering.
- Request rate limiting.
- Whitelist creation.
How to Clear Cache
When using CloudFlare, caching will occur by default, so after each site update, You’ll need to manually clear the cache. If You don’t do this, users will see the changed content for some time.
To clear cache, go to the Caching ➔ Configuration tab. The Custom Purge button will clear cache for any individual URL, while the Purge Everything button will remove all cache from Cloudflare servers, however, complete clearing will temporarily increase the number of requests to the server and the site may slow down. We recommend choosing the first option.

To avoid inconvenience for users due to outdated content, we recommend regularly clearing cache when making changes to the site.
If You frequently update information, consider setting up automatic cache clearing or reducing cached data lifetime in CloudFlare settings. This will help maintain balance between site loading speed and content relevance for visitors.