5.1.4 How to detect the source of spam on a VPS/Dedicated server. How to block mail for a specific site

Spam (junk mail) is typically the bulk sending of electronic messages that often contain promotional offers, unsolicited invitations, or fraudulent materials. Spam can be created in a variety of ways, including automated scripts on websites, compromised ssh/ftp accounts, email accounts, or specialized software tools aimed at sending mass messages. One important aspect of email server management is detecting the source of spam to prevent negative consequences such as IP addresses or domains being blocked, blacklisting, and damage to the server’s reputation. You can detect the source of spam by checking the server’s mail queue.
A mail queue on a server is a mechanism for managing the sending and delivery of email. When the server receives an email to send, it is stored in a queue and then sent to recipients via appropriate protocols such as SMTP. If sending fails due to temporary problems or congestion, the letter remains in the queue to be resent.
Each letter has a unique identifier, for example 1TrXS1-0003SL-3h, which is used for management and logging in Exim.
Additionally: when fighting unwanted mail or spam, it is important to install protection against bots in the form of a captcha for each contact form on your website. Problems often arise when spam is sent through vulnerabilities or an unsecured contact form.
An example of captcha to protect your sites from unwanted mailings.
Commands for managing the Exim mail queue
Important: commands to manage the mail queue must be executed as superuser root. They are available only for virtual and dedicated servers.
To work with the mail queue, you need to connect to the server using the SSH protocol. Further in the article the commands will be listed.
1. View mail queue:
- exim -bpc: View the number of messages in the mail queue.
- exim -bpc
root@hostname:~# exim -bpc
90
- exim -bp: The command will show a list of all messages in the queue, including their status (for example, “for dispatch” or “on hold”).
- mailq: Exactly the same as the previous
exim -bpcommand, which will display the contents mail queue. It is important to note that this command will be correct not only for Exim4, but also for other SMTP mail services: SendMail, Postfix.
- mailq
root@hostname:~# mailq
1h 8.0K 1rojOt-00049d-Mj mailbox1@domain.com
2h 3.8K 1rojlX-0002mO-Gq mailbox2@domain2.com
3h 1.8K 1roiSp-0002Ua-Qb mailbox2@domain3.com
4h 2.4K 1rog3c-0001cJ-5f mailbox2@domain2.com
- exipick -i: View the list of
idletters that are in the mailbox queues.
root@hostname~# exipick -i
1rnfUl-0001g4-6o
1ro6q2-0008Ag-0c
1ro8XY-0001OE-MG
1rog3c-0001cJ-5f
- exiqgrep -i -r “recipient’s mailbox or mail domain”: View list identifiers of letters that are in the mail queue and are addressed to the desired mailbox or domain.
Additional: for additional information, save the letter ID, for example, 1roiSp-0002Ua-Qb, which will be designated as id. This ID will be used when forming a team to obtain detailed information.
2. View information about individual letters using the letter identifier id:
- exim -Mvl id: View the log of sending a letter with the specified identifier
id, whereidis the identifier of the message from the queue list (can be found when using the Exim -bp command). Example identifier:1rog3c-0001cJ-5f.
- exim -Mvl id
- exim -Mvh id: View message headers in the mail queue. Useful in identifying mailing sources.
- exim -Mvh id
- exim -Mvb id: View the body/content of a message in the mail queue. Useful for identifying mailing sources.
- exim -Mvb id
More details: when analyzing a list of email messages, it is easy to determine the sender of an email based on the total volume of emails sent from a specific mailbox or domain. This distinctive feature helps quickly identify potential sources of spam. Additionally, to determine the source of spam, you can analyze the content, headers and logs of several suspicious emails using the appropriate commands. If spam comes from a hacked mailbox, it is recommended to disable it or change the password in the mailbox settings.
3. Clearing the mail queue:
- exim -Mrm id: This command will remove a letter from the mail queue with the specified
identifier
id.
- exim -Mrm id
- exiqgrep -i -r “recipient’s mailbox or mail domain” | xargs exim -Mrm: This command will remove from the mail queue all letters whose recipient The mailbox or domain you specified is installed.
- exiqgrep -i -r admin@domain.com | xargs exim -Mrm
- exiqgrep -i -f “sender’s mailbox or mail domain” | xargs exim -Mrm: This command will remove from the mail queue all letters whose sender the mailbox or domain you specified is installed
- exiqgrep -i -f admin@domain.com | xargs exim -Mrm**
- exipick -i | xargs exim -Mrm: This command will indiscriminately delete all messages from the mailbox. queues**.
- exipick -i | xargs exim -Mrm
Simplified method for checking mail queue
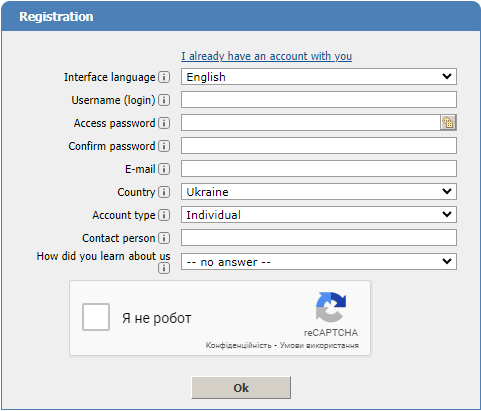
There is an easier way to view your mail queue using the control panel ISPManager4 web interface. To use this method, you must first install the Mail Queue plugin. Follow these steps:
-
Go to the control panel of the virtual or dedicated server, to the Server Settings section -> Plugins and click the Install button in the top right corner.
-
From the list, select the plugin named ispmqueue, then click Install. Confirm your choice by clicking on the appropriate checkbox and then Next.
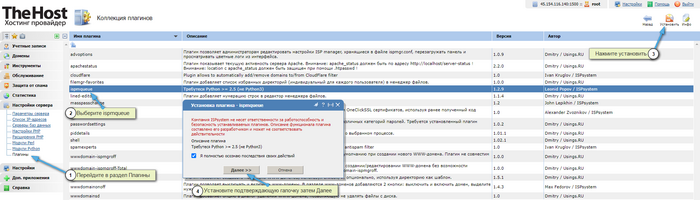
- After a few minutes, refresh the browser page and you will have a section for managing the mail queue, in the Tools -> Mail Queue category.
Important: to install the plugin, the server must have version Python >=2.5. By default, our templates have a compatible version installed. However, if you manually performed the update or plan to perform it, the Mail Queue functionality will not work.
Blocking mail
Important: To effectively block spam, it is important to understand exactly what method emails are sent. When analyzing mail messages, through the command exim -Mvh id, you can find various key points that can indicate the sending method. In particular, it is worth paying attention to the sender’s address and domain, as well as information in the message headers, which may contain information about the protocol used (for example, SMTP, PHPMail) and the sender’s server. Additionally, searching for key phrases or characteristics in the body of emails can help identify typical mailing patterns. However, to more accurately determine the sending method, additional analysis steps may be required, such as checking web server logs or application logs.
- If distribution is carried out via CRON tasks, you must delete the corresponding task in the Tools -> Scheduler (Cron) section.
- When spam is sent using mailbox, it is recommended to disable it and change the password.
- If letters are sent through site scripts, you can temporarily disable the WWW domain or completely block the sending of mail by scripts. In order to do this, you need to determine in which interpreter mode PHP your site is running:
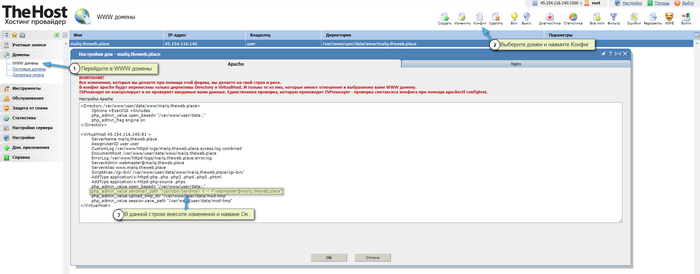
- For the PHP as an Apache module mode, in the general apache2 config (/etc/apache2/apache2.conf) of the server as root, you need to find the VirtualHost block of the desired domain and in the line.
php_admin_value sendmail_path "/usr/sbin/sendmail -t -i -f
Remove all content enclosed in double quotes (" ... ") . At the same time, do not delete the quotes themselves, you only need to delete the content that is placed in them. Or do the same in the WWW domains section in the properties of the apache2 config. After this, you need to restart the apache2 service for the changes to take effect.
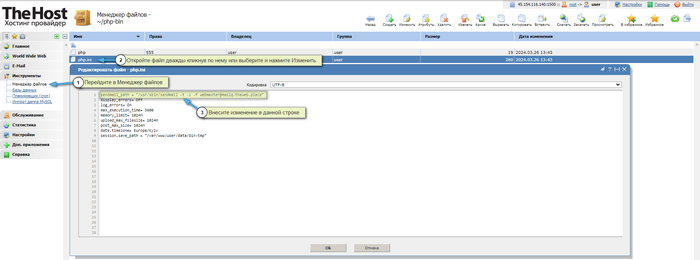
- For PHP as CGI mode, you need to go to the user access level, in the File Manager find the file
php-bin/php.ini, in the line
sendmail_path = "/usr/sbin/sendmail -t -i -f
Remove all content enclosed in double quotes (" ... ") . At the same time, do not delete the quotes themselves, you only need to delete the content that is placed in them. In this case, there is no need to reload anything, and the specified blocking will apply to all WWW domains of this user that operate in PHP CGI mode.
Важно отметить: the blocking above only applies to scripts and cron jobs used to send mail. In this case, mailboxes created on the same domain will continue to function.
Advanced methods for identifying spam senders
- This command displays a list of POST requests of all sites from the Nginx access log for the last 1000 lines. It allows you to identify malicious files or scripts that could be used for spam or other malicious activities.
- tail -n 1000 /var/log/nginx/access.log | grep POST
We inform you: the command will be useful if you found unwanted letters while checking the mailq queue, then after analyzing the contents with the exim -Mvl id command, you discovered that the sending is carried out by scripts. By checking the log /var/log/nginx/access.log it is easy to compare the time of sending the letter and the execution of the POST request by the script.
- Mailings can sometimes be carried out by hacked users who connected using the SSH protocol. To define such a user, use the command:
- ps axu | grep ssh
It will list all SSH connections to the server. Then type the command:
- w
Which will display all active connections. Typically, a user who is not in the output of this command, but is in the output of the previous one, is hacked - in this case, simply change the password of the user or his FTP account.
- The command
killall -u userwill close all open SSH connections of the user user.
- killall -u user
If instead of a user login there are numbers or an FTP account, which is not visible in Users, it can be found in the file /etc/shadow or /etc/passwd.